In the fast-paced world of IT, it’s easy to get caught in a never-ending cycle of “firefighting” – reacting to incidents as they occur, scrambling to restore services, and then moving on to the next crisis. But what if there was a better way? What if you could anticipate issues, address their root causes, and prevent them from impacting your users in the first place? This is where ServiceNow ITSM truly shines, transforming IT from a reactive support function into a proactive force for stability and innovation.
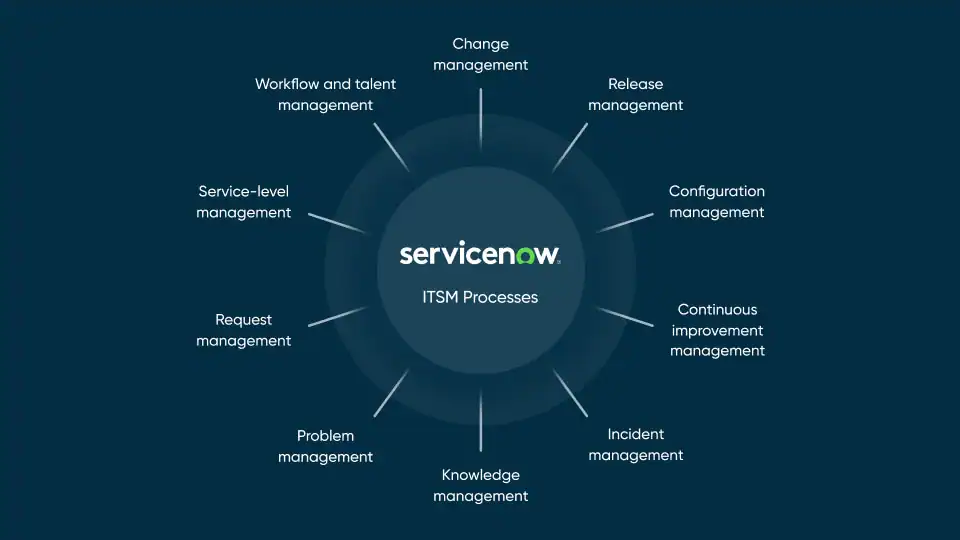
At its core, IT Service Management (ITSM) is about optimizing the delivery and support of IT services. While incident management is crucial for quickly restoring services, it’s problem management that elevates ITSM to a strategic level. And within the ServiceNow platform, problem management isn’t just a feature; it’s a powerful engine for driving proactive resolution.
The Shift from Reactive to Proactive
Imagine a scenario: Your sales application keeps crashing every few days, leading to frustrated users and lost revenue. In a reactive model, your IT team would repeatedly log incidents, troubleshoot the immediate crash, and get the application back up. However, the underlying issue remains, ready to strike again.
This is where proactive problem resolution, powered by ServiceNow ITSM, makes a significant difference. Instead of just fixing symptoms, it focuses on identifying and eliminating the root causes of recurring incidents.
How ServiceNow ITSM Enables Proactive Problem Resolution:
- Intelligent Incident Correlation and Trend Analysis: ServiceNow goes beyond individual tickets. It uses advanced analytics and even AI/Machine Learning capabilities (like Now Assist) to analyze incident data, detect patterns, and identify recurring issues. If the sales application keeps crashing, ServiceNow can flag these repeated incidents, prompting a deeper problem investigation. This moves you from “something broke” to “why does this keep breaking?”
- Structured Problem Management Workflows: ServiceNow provides a robust framework for problem management, guiding your teams through a systematic process:
- Problem Identification: Whether from trend analysis, major incidents, or monitoring alerts, potential problems are clearly identified and logged.
- Investigation and Diagnosis (Root Cause Analysis – RCA): This is the heart of proactive problem resolution. ServiceNow facilitates collaborative RCA, allowing multiple teams to contribute data and expertise to pinpoint the exact underlying cause of the issue (e.g., a software bug, a configuration error, a hardware fault).
- Workaround Documentation and Known Error Database (KEDB): While working on a permanent fix, ServiceNow allows for the documentation of temporary workarounds in the KEDB. This empowers your service desk to quickly provide solutions to users for known issues, deflecting future incidents and improving user satisfaction.
- Permanent Resolution and Change Management Integration: Once the root cause is identified, ServiceNow seamlessly integrates with its Change Management module. A change request is initiated to implement the permanent fix, ensuring all changes are controlled, approved, and minimize further risk.
- Predictive Intelligence and Event Management: Beyond reactive correlation, ServiceNow’s predictive intelligence can analyze historical data and system behaviors to anticipate potential problems before they even manifest as incidents. Integrated with IT Operations Management (ITOM) and Event Management, it can alert teams to anomalies or performance degradation that indicate an impending issue, allowing for preventive action.
- Knowledge Management as a Cornerstone: ServiceNow’s integrated Knowledge Management system is vital for proactive problem resolution. Every problem investigation, root cause analysis, and permanent fix contributes to a growing repository of knowledge. This empowers users with self-service options and equips IT teams with readily available solutions, reducing resolution times and preventing repeat investigations.
- Performance Analytics and Continuous Improvement: ServiceNow provides dashboards and reporting tools to track key metrics related to problem management, such as the number of problems identified, time to root cause analysis, and the reduction in recurring incidents. This data is crucial for identifying areas for improvement, optimizing processes, and demonstrating the tangible value of proactive IT.
The Tangible Benefits of Going Beyond Tickets:
- Reduced Incident Volume: By eliminating root causes, you significantly decrease the number of recurring incidents, freeing up your service desk.
- Improved Service Stability and Reliability: Proactive problem resolution leads to a more stable IT environment, with fewer unplanned outages and disruptions.
- Enhanced User and Customer Satisfaction: Users experience fewer issues and faster resolutions for known problems, leading to a much better overall experience.
- Cost Savings: Less time spent firefighting means reduced operational costs, fewer emergency fixes, and increased productivity.
- Increased IT Efficiency and Productivity: Your IT teams can shift their focus from reactive crisis management to strategic initiatives, innovation, and continuous service improvement.
- Better Risk Management: Identifying and addressing potential issues before they become critical strengthens your overall IT risk posture.
In conclusion, ServiceNow ITSM is more than just an incident ticketing system; it’s a comprehensive platform that empowers organizations to move beyond reactive incident management and embrace a truly proactive approach to IT service delivery. By systematically identifying and resolving the root causes of problems, ServiceNow ITSM helps IT teams transform into strategic partners, ensuring greater stability, efficiency, and satisfaction across the entire enterprise.